Configuring Distributed Cloud Firewall
This section describes the Distributed Cloud Firewall functional area of Aviatrix CoPilot.
Creating SmartGroups for Distributed Cloud Firewall
A Distributed Cloud Firewall SmartGroup contains one or more filters to identify cloud endpoints that map to an app domain. A filter specifies resource matching criteria. Matching criteria could be a cloud tag; a resource attribute (such as account name or region); or a list of IP prefixes. All conditions within the filter must be satisfied to be matched. A tag or resource attribute-based filter must be associated with a resource type (VPC/VNet, subnet, or VM).
To create a SmartGroup, see Creating SmartGroups.
Creating Distributed Cloud Firewall Policies
After creating SmartGroups, you create Distributed Cloud Firewall policies that consist of rules, to define the access control to apply on the traffic between those SmartGroups.
| If you include a WebGroup in your rule, the Destination SmartGroup must be 'Public Internet'. Also, you must select a Source SmartGroup that contains a Spoke Gateway that has local Egress enabled. |
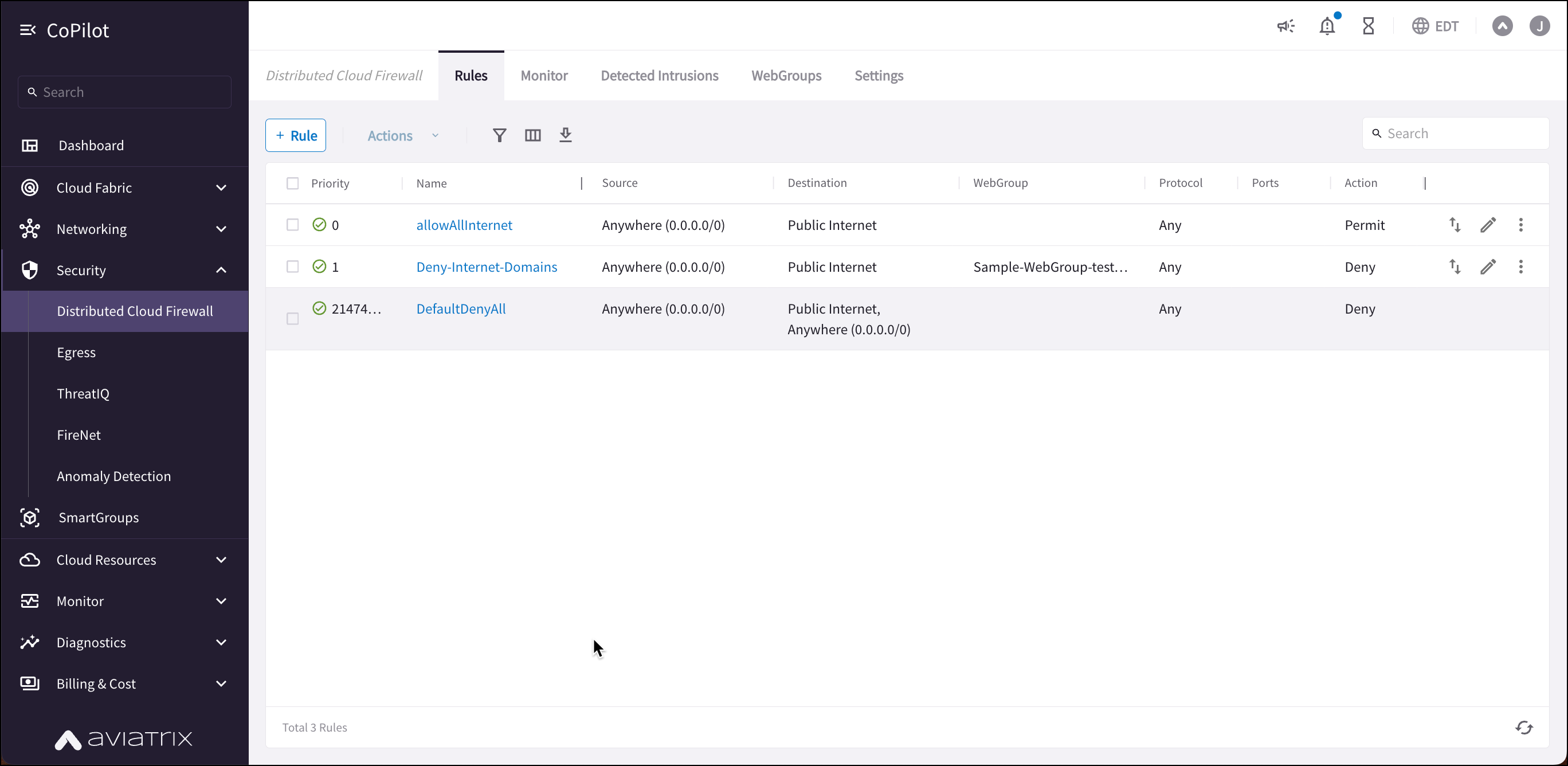
For example, in the workload isolation use case, all traffic (i.e., ports and protocols) between the ShoppingCart application and the Product Logging app must be blocked (Denied). You can decide which policies to enforce, and if you want to log the actions related to a rule. These rules are enforced (if enabled) on your Spoke gateways, and are executed against the Spoke gateways in the order that they are shown in the rule list.
Creating a rule for the workload isolation use case would resemble the following:
-
Source SmartGroup: Shopping Cart application
-
Destination SmartGroup: Product Logging app
-
Action: Deny
-
Protocol: Any
-
Ports: 0-65535 (Any)
-
Logging: Off
-
Enforcement: On
Prerequisites and Caveats
-
Make sure you are aware of the prerequisites and limitations for Intrusion Detection before creating a policy with Intrusion Detection enabled.
-
For any VNets that have Security Group Orchestration applied, and that are included in a rule that is not enforced, the application security group (ASG) in the network security group (NSG) rule remains associated with the VM even though the NSG rule using the ASG is not present.
-
Logging can consume a significant amount of disk space. You can manage disk space settings and retention settings. You can also configure how long to keep your Distributed Cloud Firewall logs.
-
A SmartGroup traffic flow can belong to more than one rule. If this occurs, the priority of the rule determines the action that is taken first.
Creating the Distributed Cloud Firewall Policy
To create a new Distributed Cloud Firewall policy:
-
In CoPilot, navigate to Security > Distributed Cloud Firewall.
-
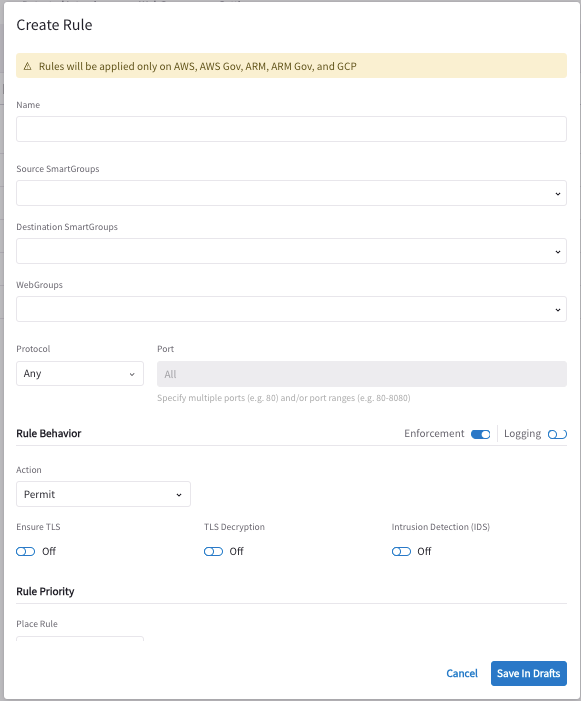
Click +Rule. The Create New Rule dialog displays.
-
Use the Distributed Cloud Firewall Field Reference to create your rule.
-
Click Save in Drafts.
| Before committing the rule, you can click the rule on the Rules tab and click Discard Change in the vertical ellipses menu to discard the most recent change (whether it was an addition, deletion, or an edit). |
-
Make additional modifications as needed by clicking the pencil icon next to the rule.
-
You can then review, commit, or discard the rule changes.
Editing a Distributed Cloud Firewall Rule
-
Click the Edit
 icon next to a rule. You can edit all rule properties.
icon next to a rule. You can edit all rule properties. -
Click Save.
Deleting a Distributed Cloud Firewall Rule
|
If a rule is not Enforced, you can safely delete it. If a rule is Enforced, and any of its Destination SmartGroups belong to a VPC/VNet that has SG Orchestration (intra-VPC) enabled, the resources related to those SmartGroups may be impacted by rule deletion, depending on how the rule is defined. |
To delete a rule:
-
Next to the applicable rule, click the vertical ellipsis
 menu and then click Delete Rule.
menu and then click Delete Rule. -
Click Commit to delete the rule. You can click Discard if you want to keep the rule.
Retaining Distributed Cloud Firewall Log Files
To configure how many days to keep your Distributed Cloud Firewall logs, in CoPilot navigate to Settings > Resources > Disk Utilization and scroll down to Distributed Cloud Firewall Logs. Use the slider to select the number of days to retain your logs (default is five days).
| Aviatrix recommends not logging Permit rules. |
Viewing Distributed Cloud Firewall Rule Statistics
You can open a previously created rule to view the statistics related to the execution of that particular rule. You can view traffic statistics from the last hour, week, or month, or a custom time period. The resulting graph indicates if the traffic is Observed, Enforced & Allowed, or Enforced & Denied.
Resetting Traffic Count
On the Policy tab, you can select a rule and then click the vertical ellipses ![]() to select Reset Traffic Count. This resets the traffic count statistics for that rule.
to select Reset Traffic Count. This resets the traffic count statistics for that rule.
Distributed Cloud Firewall Monitoring
Under Security > Distributed Cloud Firewall > Monitor, you can filter packet logs for Distributed Cloud Firewall rules that have logging enabled, to determine why a rule may not be working as intended.
You can filter based on the following information: timestamp, rule, source/destination IPs, protocol, source/destination port, action (allowed or dropped), and if the rule is enforced. The table refreshes every 15 seconds, and you can also refresh the table manually.
CoPilot throttles the logs for each connection shown on the Monitor tab to one packet per minute in each direction.
You can click Save View or Save As after filtering your log data. The saved views are then available from a second drop-down on the Performance page.
After selecting a saved view, you can:
-
Clear it and select another saved view
-
Select new metrics/gateways and create or save another view
You can also manage your available views.
Configuring the Polling Interval
| Lowering the polling interval can create more load on the Controller. The default setting should be sufficient. |
The Aviatrix Controller periodically polls your clouds to gather and inventory its resources. For example, if you modified your Cloud Tags, you may want to poll data more frequently so that CoPilot reflects those changes.
-
In CoPilot go to Security > Distributed Cloud Firewall > Settings. The CSP Resource Polling slider is On by default.
-
Enter the desired polling interval in minutes (default is 15). This can be a value between 1-1440.
| Toggle off the CSP Resource Polling slider if you do not want the Controller to periodically poll your CSP resources. |
You can manually trigger a poll to fetch resources directly from your CSPs by clicking Refetch CSP Resources on the SmartGroups tab. The poll may take several minutes to complete depending on the size of your environment.
Distributed Cloud Firewall Supported Capabilities
| Capability | 6.7 | 6.8 | 6.9 | 7.0 | 7.1 |
|---|---|---|---|---|---|
Distributed Cloud Firewall is supported in the following cloud providers: |
AWS, Azure |
AWS, AWS GovCloud, Azure, Azure Government, and GCP |
AWS, AWS GovCloud, Azure, Azure Government, and GCP |
AWS, AWS GovCloud, Azure, Azure Government, and GCP |
AWS, AWS GovCloud, Azure, Azure Government, and GCP |
Configure up to 500 SmartGroups |
x |
x |
x |
x |
x |
Up to 3000 CIDRs per SmartGroup |
x |
x |
x |
x |
x |
Number of rules per policy |
64 |
2000 |
2000 |
2000 |
2000 |
Number of port ranges |
1 |
64 |
64 |
64 |
64 |
Overlapping IPs* |
x |
x |
|||
x (Azure - Preview) |
x (AWS - Preview and Azure - GA) |
Unless otherwise indicated the feature is GA on the indicated cloud.
*Distributed Cloud Firewall (DCF) understands any defined SNAT/DNAT rules and updates the address for each gateway, enforcing the DCF rules.