Onboarding Your Google Account
Introduction
Before creating a Google Cloud account for the Aviatrix Controller, follow the steps below to make sure you have the credentials set up for API calls.
-
Create a Google account (https://cloud.google.com/).
Continue to the next step if you have already done so.
The Controller supports multiple accounts with each account associated with a different Google project, but there needs to be at least one account to start with.
-
Create a Google Project.
Enabling Compute Engine API on the Selected Project
-
Go to your Google Cloud Platform (GCP) console, click on the dropdown menu in the top left, and select APIs and Services.
-
At the Dashboard, click Enable APIs and Services.
-
In the Search box, enter "Compute Engine API" and select it from search results.
-
Click Enable.
Creating a Credential File
When you create a cloud account on the Aviatrix Controller for GCP, you will upload a Google Cloud Project Credentials file. Follow the steps below to download the credential file from the Google Cloud Console.
You need a JSON key file for the service account. This file provides the necessary credentials to manage GCP resources.
To create a key file for your GCP project, follow these steps:
-
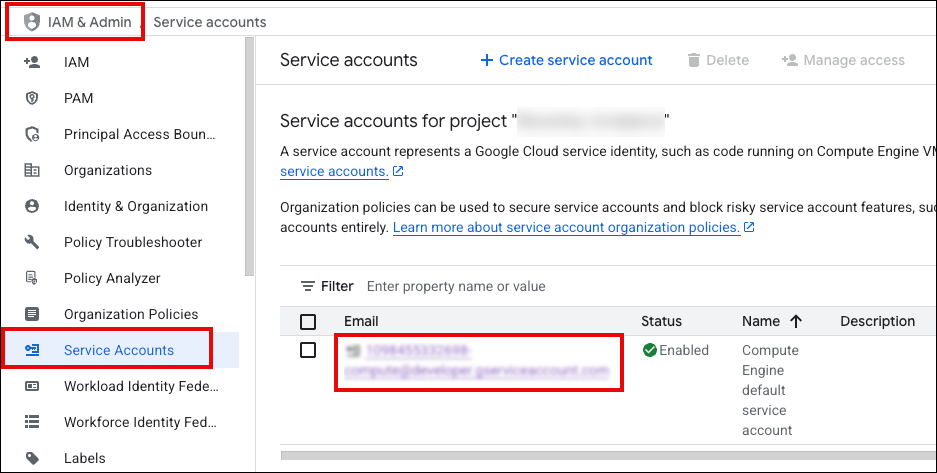
In the GCP Console, go to IAM & Admin > Service Accounts.
-
(Optional) Create a service account that has the necessary permissions to manage GCP resources.
You do not need to create a service account if you already have one with the required permissions.
-
In the table, click the Email (name) for the service account you want to use.
-
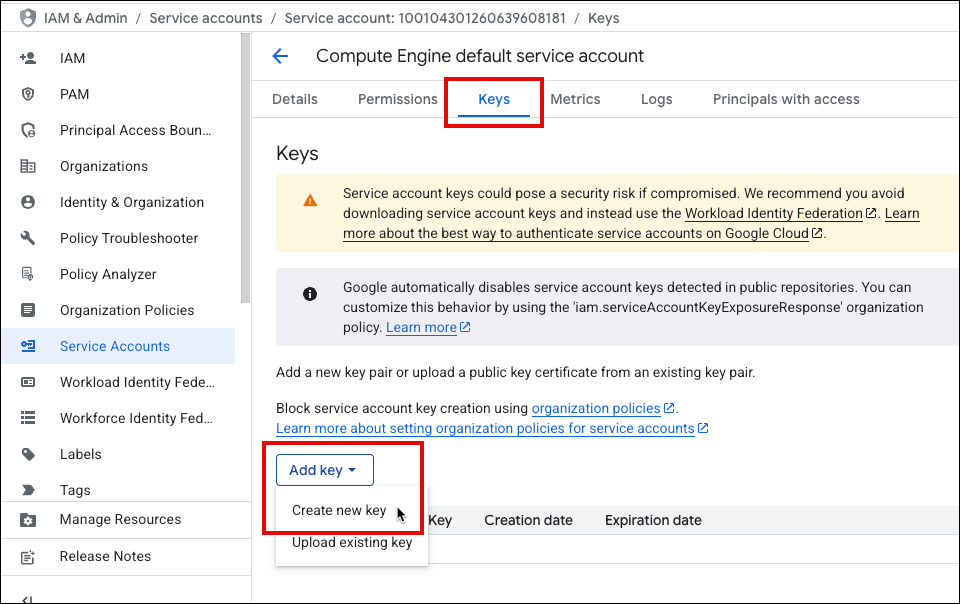
Click Keys and then click Add Key > Create New Key.
-
Select JSON as the key type and click Create.
The JSON key file is downloaded to your local machine.
Save the JSON key file securely, as it contains sensitive information that should not be shared publicly.
Creating a Service Account with Restricted Access
We recommend creating the service account with the Editor role as mentioned. But in some cases an organization might want to further restrict permission for the service account. In such a situation Aviatrix recommends at least the following roles assigned to the service account so Aviatrix can perform its functions properly, such as managing the compute resources, route tables, firewall rules, shared service VPC network, etc.
-
Compute Admin
-
Service Account User
-
Organization Administrator (required for GCP Shared VPC)
-
Project IAM Admin (required for GCP Shared VPC)
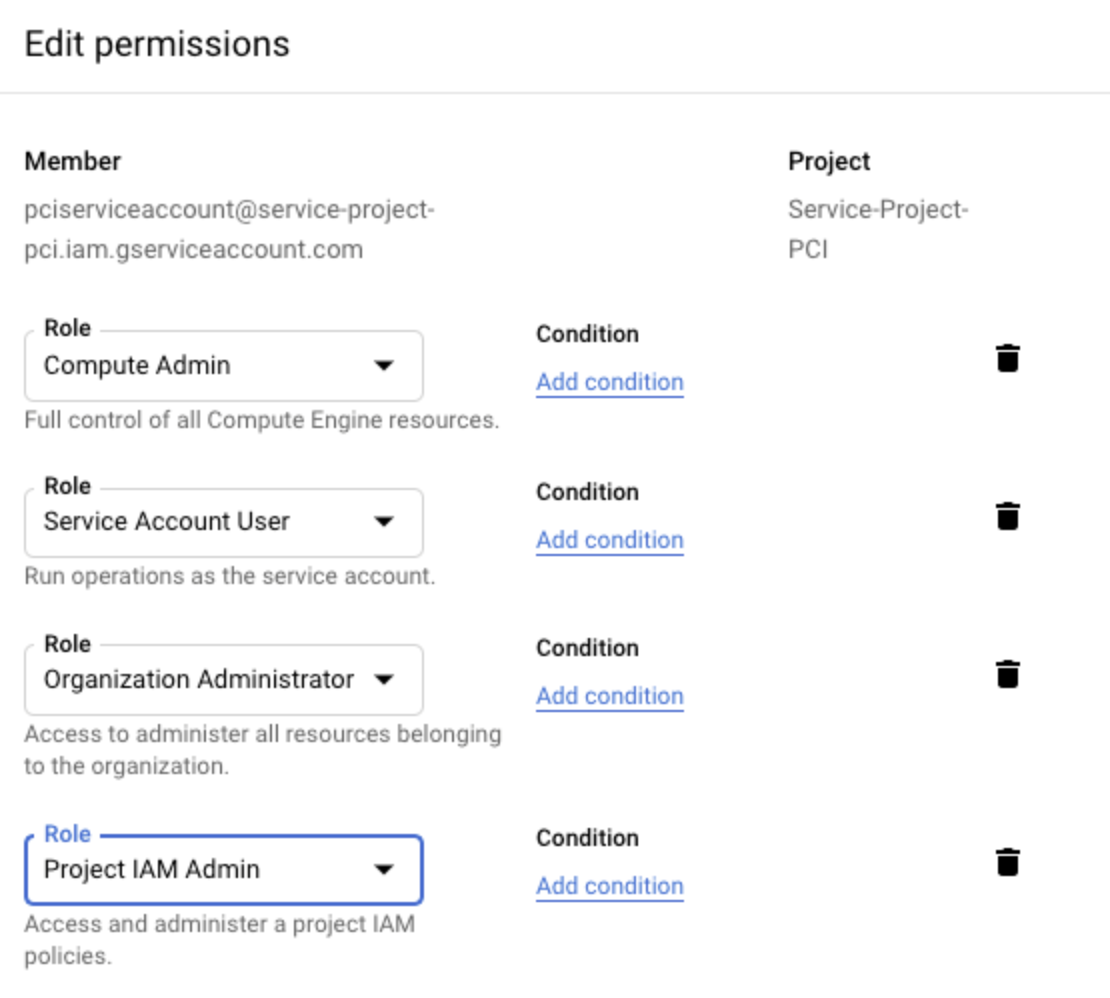
If an organization is currently using GCP Shared VPC or planning to use in future, then enabling Organization Administrator and Project IAM Admin is also required.
In addition to restricting the GCP roles, you can restrict the rights for those roles. You can grant roles permission to perform the following tasks:
compute.addresses.create compute.addresses.createInternal compute.addresses.delete compute.addresses.deleteInternal compute.addresses.get compute.addresses.list compute.addresses.use compute.addresses.useInternal compute.disks.create compute.disks.get compute.firewalls.create compute.firewalls.delete compute.firewalls.get compute.firewalls.list compute.firewalls.update compute.forwardingRules.create compute.forwardingRules.delete compute.forwardingRules.list compute.globalOperations.get compute.healthChecks.create compute.healthChecks.delete compute.healthChecks.useReadOnly compute.httpHealthChecks.create compute.httpHealthChecks.get compute.httpHealthChecks.useReadOnly compute.images.list compute.images.useReadOnly compute.instanceGroups.create compute.instanceGroups.delete compute.instanceGroups.get compute.instanceGroups.update compute.instanceGroups.use compute.instances.create compute.instances.delete compute.instances.get compute.instances.list compute.instances.setDeletionProtection compute.instances.setMachineType compute.instances.setMetadata compute.instances.setTags compute.instances.start compute.instances.stop compute.instances.updateNetworkInterface compute.instances.use compute.licenses.get compute.networks.addPeering compute.networks.create compute.networks.delete compute.networks.get compute.networks.list compute.networks.listEffectiveTags compute.networks.removePeering compute.networks.updatePolicy compute.projects.get compute.projects.setCommonInstanceMetadata compute.regionBackendServices.create compute.regionBackendServices.delete compute.regionBackendServices.get compute.regionBackendServices.update compute.regionBackendServices.use compute.regionOperations.get compute.routes.create compute.routes.delete compute.routes.list compute.subnetworks.create compute.subnetworks.delete compute.subnetworks.get compute.subnetworks.list compute.subnetworks.use compute.subnetworks.useExternalIp compute.targetPools.addInstance compute.targetPools.create compute.targetPools.delete compute.targetPools.get compute.targetPools.removeInstance compute.targetPools.use compute.zoneOperations.get compute.zones.list iam.serviceAccounts.actAs logging.logEntries.create pubsub.subscriptions.consume pubsub.subscriptions.create pubsub.subscriptions.delete pubsub.subscriptions.get pubsub.topics.attachSubscription pubsub.topics.create pubsub.topics.delete pubsub.topics.get pubsub.topics.publish resourcemanager.projects.get
If you want to monitor egress traffic on a GCP cloud account, ensure that the following APIs are enabled to grant the required GCP Resource Manager and GCP Container permissions:
container: container.googleapis.com cloud Resource Manager: cloudresourcemanager.googleapis.com
For more information about requirements for monitoring egress traffic on GCP, see Implementing Egress in an Aviatrix-Managed Network.
GCP requires the following permissions to discover and connect to GKE clusters:
container.clusters.list container.endpointSlices.list container.namespaces.list container.nodes.list container.pods.list container.services.list
For more information about Kubernetes Engine (GKE) requirements, see Kubernetes Prerequisites and Permissions.
Onboarding your GCP Account in Your Controller
To onboard this GCP account into your Aviatrix Controller, use the following steps.
-
Open your Controller and go to Onboarding > click Google Cloud Platform.
-
Under Enter Aviatrix Customer ID, enter the customer ID you received in an email.
-
Skip the Enter Certificate Domain field.
-
Under Create Primary Access Account, enter the following information.
| Parameter | Description |
|---|---|
Account Name |
Enter a clear Account Name. |
Project ID (Optional) |
In the Project ID field, enter the name of the Gcloud project for this account. |
Project Credentials |
Click Choose file and choose the correct JSON file downloaded from your GCP account. |
-
Click Create.
Onboarding Multiple GCP Service Accounts
The Controller supports multiple Service Accounts from different Google Cloud projects. Onboard each GCP account separately using a unique Account Name, the correct Project ID for each project, and the JSON credentials file from the main Management Account.
For example, you may need to set up a Service Account in the first or Management GCP Project, and then give that Service Account access to a second Gcloud Project where they can deploy gateways.
-
First, in your GCP account, create the primary Management Project and the secondary project.
-
Create a Service Account from within the Management Project.
-
Generate a JSON credential file that gives the Service Account permission to access the secondary project.
This JSON file is the credentials file you will use while onboarding this account in your Controller.
-
Log into your Controller and go to Onboarding > Google Cloud Platform and do the following:
-
Enter a clear Account Name.
-
Enter the Management Project Name as the Project ID.
-
Upload the JSON credentials file.
-
Click Create.
-
-
Next, onboard the secondary account.
-
Enter a clear Account Name that helps you distinguish these projects.
-
Enter the secondary project’s ID as the Project ID.
-
Upload the same JSON credentials file from the primary Management Project.
-
Click Create.
-
Now, your Controller has access to the Management Project and the secondary project where you can deploy gateways.
Troubleshooting Tips
If the cloud account creation fails, check the error message on Aviatrix CoPilot and try again with the steps provided in this document.
For additional support, please open a support ticket at the Aviatrix Support Portal.