Creating Distributed Cloud Firewall Policies
After creating SmartGroups, you create Distributed Cloud Firewall policies that consist of rules, to define the access control to apply on the traffic between those SmartGroups.
| If you include a WebGroup in your rule, the Destination SmartGroup must be 'Public Internet'. Also, you must select a Source SmartGroup that contains a Spoke Gateway that has local Egress enabled. |
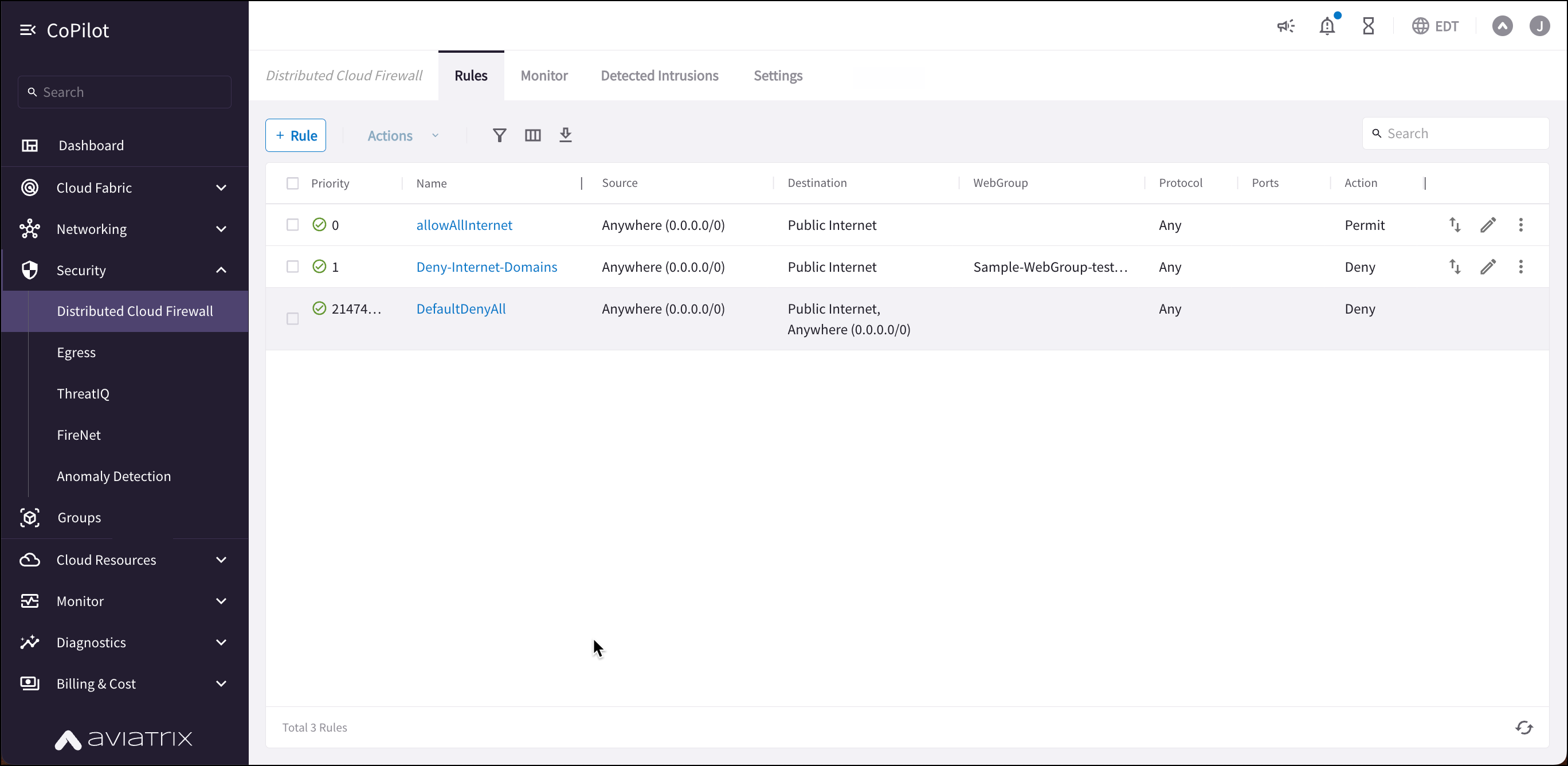
For example, in the workload isolation use case, all traffic (i.e., ports and protocols) between the ShoppingCart application and the Product Logging app must be blocked (Denied). You can decide which policies to enforce, and if you want to log the actions related to a rule. These rules are enforced (if enabled) on your Spoke gateways, and are executed against the Spoke gateways in the order that they are shown in the rule list.
Creating a rule for the workload isolation use case would resemble the following:
-
Source SmartGroup: Shopping Cart application
-
Destination SmartGroup: Product Logging app
-
Action: Deny
-
Protocol: Any
-
Ports: 0-65535 (Any)
-
Logging: Off
-
Enforcement: On
Prerequisites and Caveats
-
Make sure you are aware of the prerequisites and limitations for Intrusion Detection before creating a policy with Intrusion Detection enabled.
-
For any VNets that have Security Group Orchestration applied, and that are included in a rule that is not enforced, the application security group (ASG) in the network security group (NSG) rule remains associated with the VM even though the NSG rule using the ASG is not present.
-
Logging can consume a significant amount of disk space. You can manage disk space settings and retention settings. You can also configure how long to keep your Distributed Cloud Firewall logs.
-
A SmartGroup traffic flow can belong to more than one rule. If this occurs, the priority of the rule determines the action that is taken first.
Creating the Distributed Cloud Firewall Policy
To create a new Distributed Cloud Firewall policy:
-
In CoPilot, navigate to Security > Distributed Cloud Firewall.
-
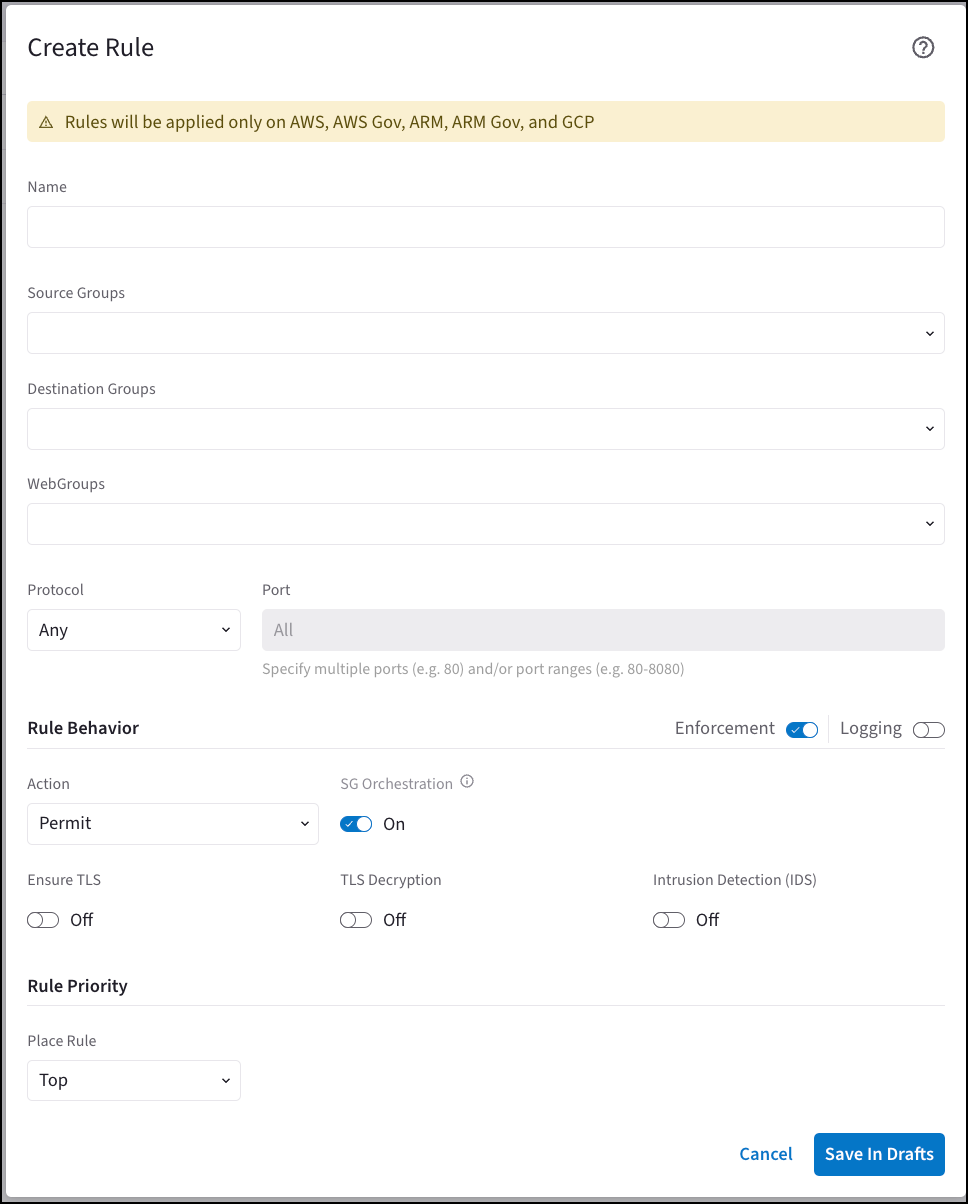
Click +Rule. The Create New Rule dialog displays.
-
Use the Distributed Cloud Firewall Field Reference to create your rule.
-
Click Save in Drafts.
| Before committing the rule, you can click the rule on the Rules tab and click Discard Change in the vertical ellipses menu to discard the most recent change (whether it was an addition, deletion, or an edit). |
-
Make additional modifications as needed by clicking the pencil icon next to the rule.
-
You can then review, commit, or discard the rule changes.
Editing a Distributed Cloud Firewall Rule
-
Click the Edit
 icon next to a rule. You can edit all rule properties.
icon next to a rule. You can edit all rule properties. -
Click Save.
Deleting a Distributed Cloud Firewall Rule
|
If a rule is not Enforced, you can safely delete it. If a rule is Enforced, and any of its Destination SmartGroups belong to a VPC/VNet that has SG Orchestration (intra-VPC) enabled, the resources related to those SmartGroups may be impacted by rule deletion, depending on how the rule is defined. |
To delete a rule:
-
Next to the applicable rule, click the vertical ellipsis
 menu and then click Delete Rule.
menu and then click Delete Rule. -
Click Commit to delete the rule. You can click Discard if you want to keep the rule.