VPN User Anonymous Internet Surfing
There are a number of ways that administrators can identify visitors to their websites: web browser “user-agent” strings; 1st and 3rd party cookies; source IP addresses; and more. Source IP addresses often provide both geographic location and company information about visitors. This document describes how to change the source IP address seen by websites by building a simple VPN solution with Aviatrix User VPN. When configured correctly, websites will see the source IP as belonging to AWS and not the end user.
Configuration Workflow
Pre-Configuration Checklist
-
Deploy and configure both an Aviatrix Controller and CoPilot instance.
-
Install the Aviatrix User VPN Client on the user machine.
Configuration Steps
-
Create a new VPC in AWS in CoPilot.
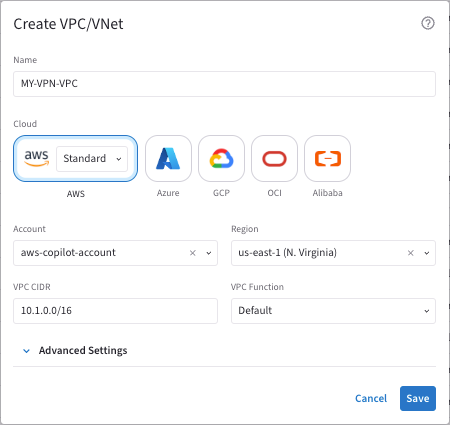
This example uses 10.1.0.0./16 for the VPC CIDR.
-
Create a VPN Gateway in the newly established VPC.
When creating the VPN Gateway ensure that the Split Tunnel feature is disabled so that all Internet traffic is forced through this VPN. -
Create a VPN user associated with the Aviatrix VPN Gateway and set the Base Policy to Allow All.
-
On the UserVPN > Users tab, click the vertical ellipsis
 next to the VPN user you just created and select Download Client Certificate.
next to the VPN user you just created and select Download Client Certificate. -
In the Aviatrix VPN User Client, install the client certificate by clicking the + icon at the bottom of the window.
-
Connect to the newly created VPN.
-
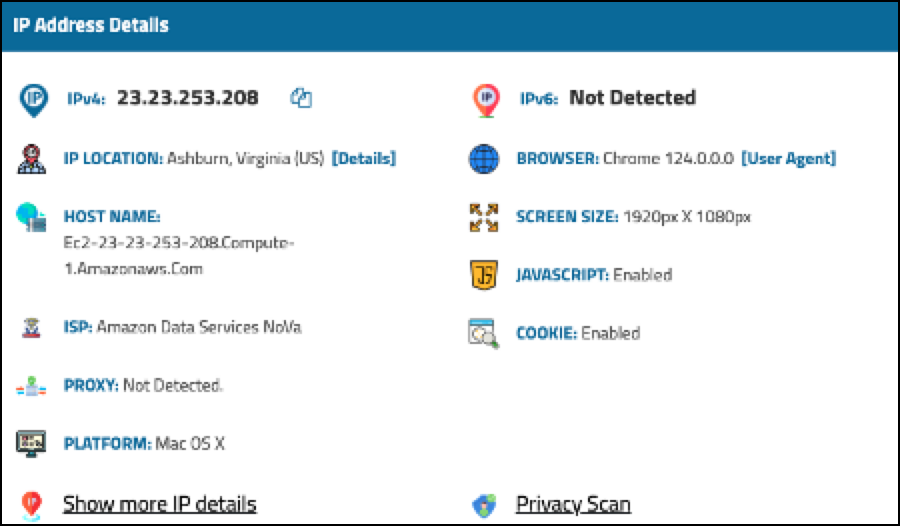
After connection occurs (Status: Connected), visit a website to check your IP address. The IP address should show as coming from Amazon AWS and not your true source address.
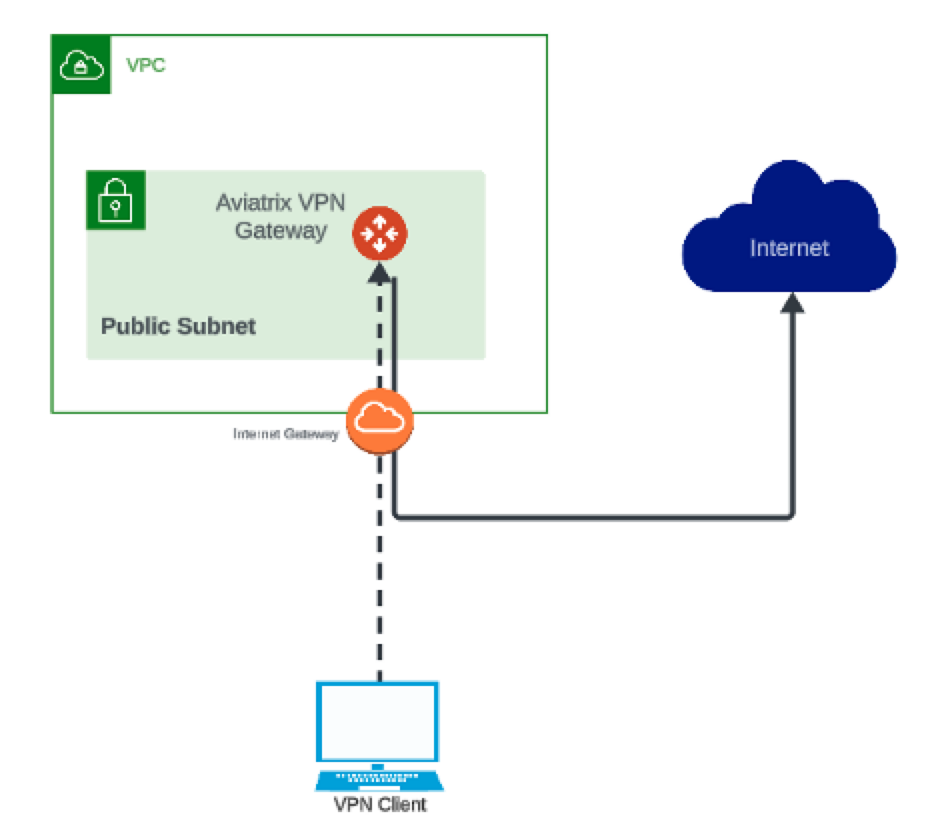
Traffic Flow
The client VPN connects to the Aviatrix VPN Gateway in AWS, which then forwards web requests to the Internet. This masks the end user IP address of an AWS EC2 instance (running as an Aviatrix VPN Gateway).
| No method is fail-safe in protecting user identity when surfing the Internet. In addition to masking your IP address, consider combining other protections like using your web browser “Incognito” mode, and browser plugins that mask web-browser user-agent strings that identify your operating system and browser type. |