Implementing Network Segmentation with Aviatrix Edge
This document describes the Aviatrix Secure Edge solution for virtual LAN (VLAN) network segmentation.
Before reading this document, you should be familiar with the following:
-
Aviatrix Multicloud Transit Network architecture
-
Aviatrix ActiveMesh
-
Aviatrix Gateway High-Availability
-
Virtual LAN networking concepts
-
Virtual Router Redundancy Protocol (VRRP) concepts
Topology
The topology below illustrates a site with single VLAN, Virtual Router Redundancy Protocol (VRRP), and two Edge Gateways deployed with high-availability (HA).
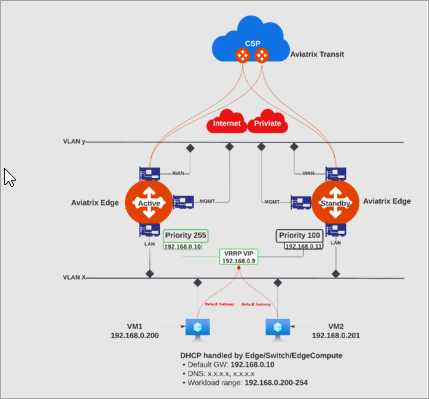
| VRRP is applicable when the Aviatrix Edge Gateway is deployed as the default gateway for a single VLAN or multiple VLANs and requires Edge Gateway HA. |
Multiple Virtual LAN Segmentation
Virtual Local Area Networks (VLANs) enables you to create network segmentation to maintain separation between Local Area Networks. Businesses may deploy network segmentation for additional security or to keep workloads in their network separate.
Aviatrix Edge supports multiple VLANs architecture. This capability enables you to segment your on-premise network traffic for your LAN network segments. For example, you can segment the workload in the cloud that supports PoS (Point-of-Sale) application to the PoS application at the Edge in that specific LAN segment only.
The diagram below illustrates a site with multiple VLAN segments.
In this diagram:
-
A VLAN segment is configured per Edge Gateway.
-
The LAN side network segments are created symmetrically on both the active and standby Edge Gateways in a site.
-
Each VLAN segment is associated with a virtual interface named as “ethx.<_VLANID_>” on both the active and standby Edge gateways.
-
A VLAN segment configuration is comprised of a VLANID, Primary IP, Secondary IP, Subnet mask and Virtual IP.
-
The Virtual IP is used by the LAN hosts as the default gateway IP for the VLAN segment.
-
The Edge gateway provides the trunk interface connectivity to the LAN side switch.
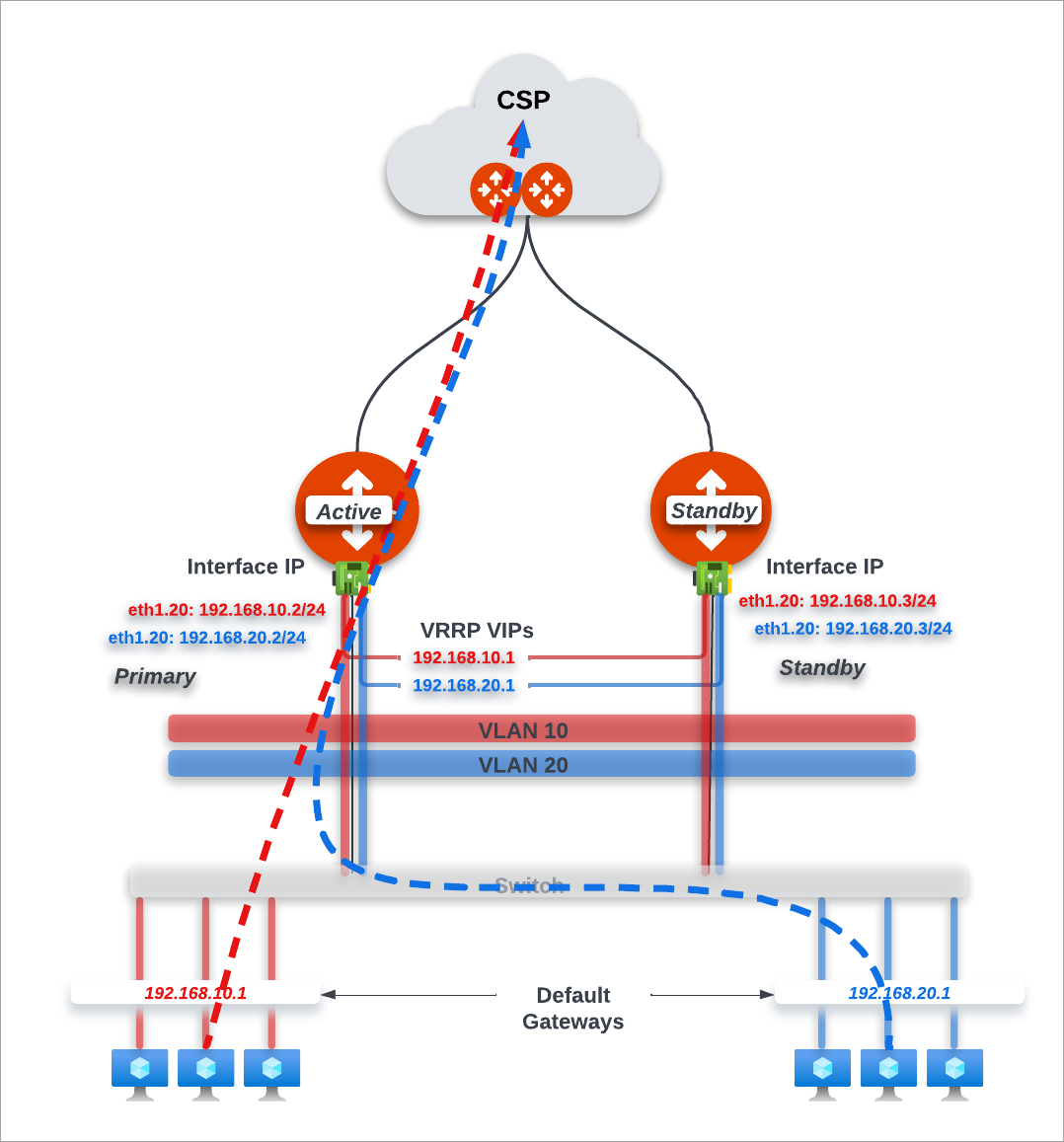
You can deploy an Edge Gateway in high-availability active-active or active-standby mode (see Enabling Edge Gateway High Availability). The Edge Gateways advertise the CIDRs associated with the VLAN segments to the Aviatrix Transit Gateways.
Associating VLANs to Aviatrix Network Domains
Aviatrix Edge enables you to segment your on-premise network traffic through network domains and connection policies. The Edge Gateway routes on-premise and inter-VLAN traffic flow based on the network domain connection policies.
This diagram illustrates on-prem network traffic flow between the yellow and orange domains that are segmented.
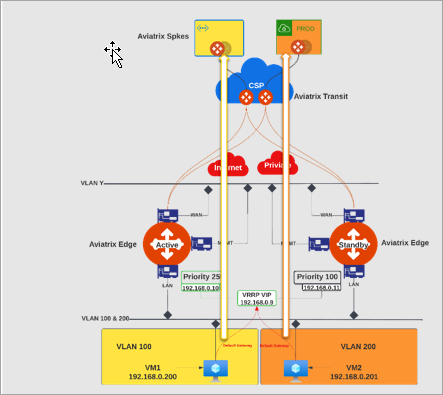
To segment the on-premise network traffic, you must associate the VLAN segment and its workload in the CSP to the same network domain. For example:
-
VLAN 100 is associated to the same network domain as its workload in the CSP.
-
VLAN 200 is associated to the same network domain as its workload in the CSP.
To associate VLANs to Aviatrix Network Domains:
-
Go to Networking > Network Segmentation > Network Domains tab.
-
To add a new network domain, click + Network Domain.
Provide the following information:
Setting Description Name
Enter a unique name for this network domain.
A network-domain name can only have letters, digits, a hyphen (-), and an underscore (_). The name must start with a letter and must have 2-27 characters. For example, Dev_Domain.
After you create and save a network domain, you cannot change its name. Association
From the dropdown list, select the Spoke VPC/VNet and the VLAN that are in this network domain.
Connect to Network Domain
To connect this network domain to other network domain, from the dropdown list, select the other network domain.
This enables traffic flow between both network domains.