Adding FireNet to a Transit Gateway
When FireNet is added to a Transit gateway, a firewall can be inserted into the Aviatrix Transit VPC/VNet. East-west and egress traffic is inspected by these firewalls, unless traffic inspection is explicitly disabled (by using an Egress FireNet or disabling the Traffic Inspection option).
|
Ensure you have completed any prerequisites before beginning. After adding FireNet to a Transit gateway you can: |
Configuration Steps
-
On the FireNet tab, click +Add FireNet.
You can also add these FireNet types:
-
Egress FireNet: ensure that a Transit gateway (new or previously created) sends traffic to the Internet and does not perform any traffic inspection.
-
AWS TGW FireNet: add FireNet functionality to your AWS Transit Gateway (TGW).
-
-
In the Add FireNet to Transit Gateway dialog, select if you want to add FireNet to an existing Transit gateway or on a new Transit gateway.
If you are adding FireNet to an existing Transit gateway that has the BGP over LAN slider On, that Transit gateway must also have DNAT/SNAT configured. Only Transit gateways that have the Transit Egress Capability toggle enabled (selected when you create a Transit gateway from Cloud Fabric > Gateways > Transit Gateways) are displayed in the Existing Transit Gateway List.
-
If creating a new Transit gateway, enter a name in the Name field.
-
Configure the following:
Field Description Cloud (prepopulated if creating on an existing Transit gateway)
Select Cloud type:
AWS: Standard, GovCloud, China
Azure: Global, GovCloud, China (same as above)
GCP
OCI
Name (new Transit gateway only)
Name for the FireNet
Account (pre-populated if creating on an existing Transit gateway)
Cloud Account Name
Region (pre-populated if creating on an existing Transit gateway) (AWS, Azure, OCI only)
Region in which to create the Transit gateway.
VPC/VNet (pre-populated if creating on an existing Transit gateway)
VPC/VNet where the Transit gateway will be deployed.
Instance Size (regardless of type of FireNet)
Minimum sizes:
AWS: c5.xlarge
Azure: Standard_B2ms
GCP: n1-standard_1
OCI: VM.Standard2.4
The minimum size may vary if HPE is enabled.
High Performance Encryption (HPE)
Turn On HPE for the FireNet deployment, for higher throughputs.
Instances
Availability Domain (OCI only): Select the OCI domain within the region (selected above).
Attach to Subnet: FireNet is launched in this public subnet.
Add a second Instance row for the High Availability (HA) instance.
Zone (GCP only): Zone in which to create the gateway.
Fault Domain (OCI only): OCI failover mechanism (see here).
Public IP: Allocate a new, static public IP address to the new Transit gateway.
Primary FireNet (AWS only)
Select if you want this FireNet to be the Primary FireNet where firewalls are attached.
Not applicable for Egress FireNet.
Secondary FireNet (AWS only)
Select if you want this to be a Secondary FireNet that will send traffic to the Primary FireNet to be inspected.
Egress and traffic inspection are disabled when Secondary FireNet is selected.
Not applicable for Egress FireNet.
Attach Secondary FireNets (AWS/Primary FireNet only)
Select the Secondary FireNets to attach to this Primary FireNet.
Not applicable for Egress FireNet.
Attach to Primary FireNet (AWS/Secondary FireNet only)
Select the Primary FireNet to which to attach this Secondary FireNet.
Not applicable for Egress FireNet.
Gateway Load Balancer (GWLB)
Slide On to enable the AWS Gateway Load Balancer (differs from the Native AWS Load Balancer, which is part of the AWS TGW FireNet workflow).
This toggle is Off by default for Azure, GCP, and OCI.
In Azure and GCP, load balancers are created automatically after FireNet is added to the Transit gateway.
Traffic Inspection
If turned Off the FireNet gateway loops back all packets.
Off by default if adding an Egress FireNet. This means that only egress traffic will be inspected/routed to a firewall.
If creating an AWS Transit Gateway with Secondary FireNet selected, Traffic Inspection is Off by default, and hidden.
Egress
Enable Egress (Internet-bound) traffic inspection.
On by default if adding an Egress FireNet.
If creating an AWS Transit Gateway with Secondary Transit selected, Egress is Off by default, and hidden.
-
Click Add.
If you are attaching Secondary FireNets to Primary (AWS only), the Attach Secondary FireNet to Primary FireNet dialog displays.
You can check the FireNet creation progress on the Monitor > Notifications > Tasks tab.
Egress FireNet
A Transit Gateway that has Egress FireNet added receives egress traffic from attached Spoke Gateways and then sends that traffic via any attached firewalls to the Internet. Egress FireNet does not inspect east-west or north-south traffic.
|
An Egress FireNet cannot be used in an external connection. It also cannot peer with other Transit Gateways. |
The Gateway Load Balancer option is configurable as follows, depending on the cloud provider:
-
AWS: Can turn On or Off
-
Azure, GCP: On by default
-
OCI: Off by default
AWS TGW FireNet
You can add AWS TGW FireNet to an AWS Transit gateway or to the Native AWS Gateway Load Balancer.
| Field | Value |
|---|---|
Add AWS TGW FireNet To |
Transit Gateway Native AWS Gateway Load Balancer |
Transit Gateway |
Select a new or existing AWS Transit gateway |
Name |
Enter a name for the new AWS TGW Transit gateway (pre-populated if you select an existing AWS Transit gateway) |
Account |
Cloud Account Name |
Region |
Region in which to create the AWS TGW Transit gateway. |
VPC |
Transit Gateway: VPC where the AWS TGW Transit gateway will be deployed. Native AWS Gateway Load Balancer: VPC where the Load Balancer will be deployed. |
Instance Size |
c5.xlarge is the recommended minimum |
High Performance Encryption |
Turn On HPE for the FireNet deployment, for higher throughputs. |
Attach to Subnet |
The AWS TGW FireNet is launched in this public subnet. |
Public IP |
The public IP address for this gateway. |
FireNet Configuration |
Gateway Load Balancer Traffic Inspection Egress See the previous table for these field descriptions. AWS TGW Firewall Domain: Select a previously configured AWS TGW Firewall Domain. The Aviatrix Firewall Domain is a FireNet-dedicated Network Domain. The AWS TGW FireNet is deployed in this domain. |
Attaching Secondary FireNet to Primary FireNet (AWS only)
Click here for more information on Primary and Secondary FireNet.
If you created and saved a Primary FireNet configuration that included Secondary FireNet attachments, after saving you are prompted to attach your Secondary FireNet to Primary.
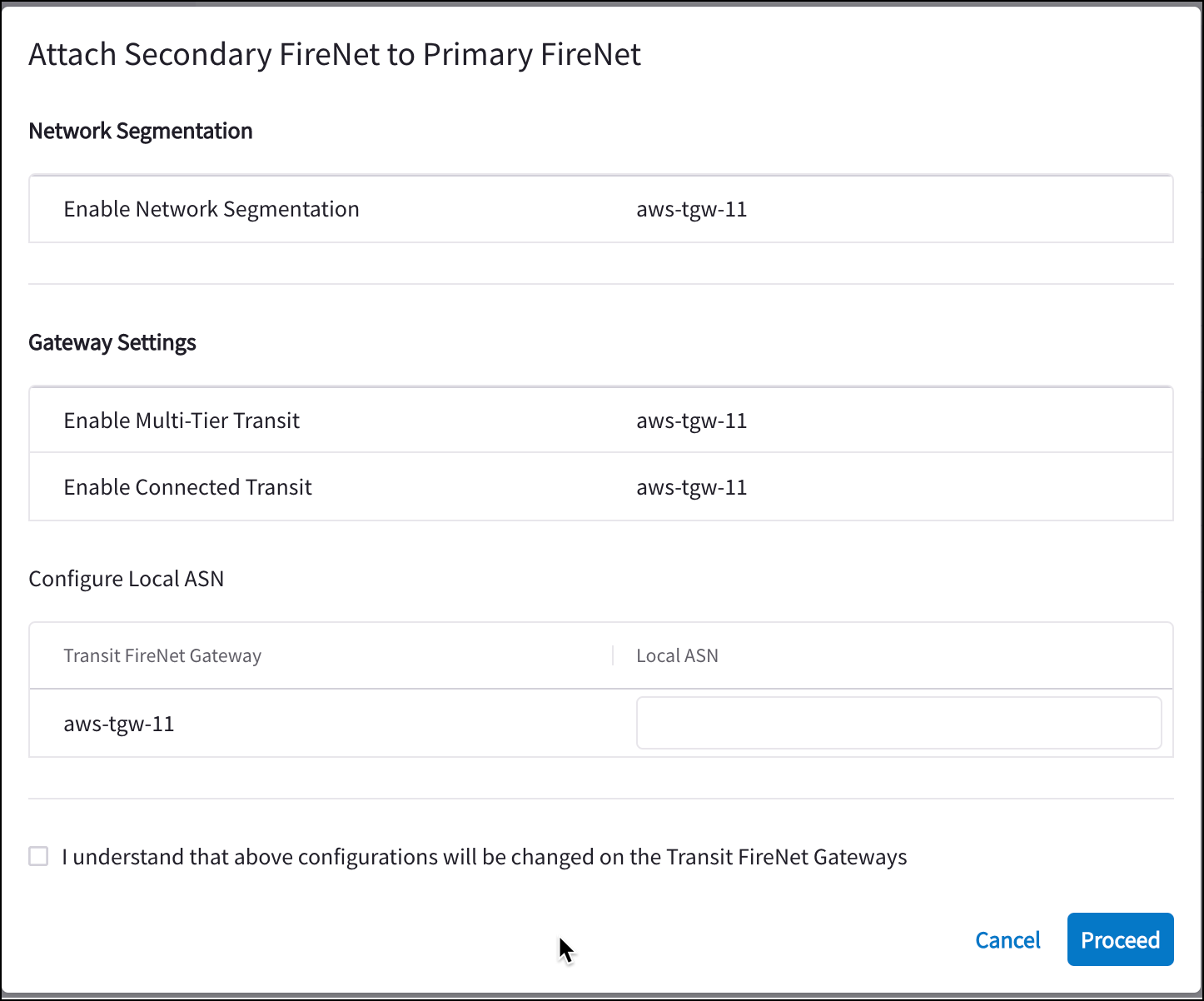
-
Confirm that the Network Segmentation and Gateway Settings information is correct for this Primary/Secondary attachment.
-
Enter the Local ASN number for the FireNet gateways (Primary and Secondary). This is the ASN of the BGP device on your side of the connection.
-
Select the checkbox to indicate your acceptance of configuration changes on the Transit FireNet gateways.
-
If the configuration is satisfactory, click Proceed. If not, click Cancel and edit your FireNet configuration.