Migrating a CSR Transit to AWS Transit Gateway (TGW)
This document assumes that you have deployed a CSR Transit solution with Transit hub CSR instances and VGWs in Spoke VPCs. The steps below provide instructions to migrate a live CSR deployment to Aviatrix with the Transit Gateway Orchestrator.
The objectives here are:
-
No change to any on-prem network.
-
No change to the connectivity between AWS VGW and on-prem. (either over DX or over Internet or both)
-
Re-use AWS VGW deployed in CSR based Transit hub VPC if possible.
-
No change to existing VPC infrastructure.
-
Minimum operation downtime.
There are a couple of patterns during the migration phase, consider the one that meets your requirements.
|
This document assumes you have already launched an Aviatrix Controller. |
Before the migration process starts, plan out what network domains you need to create and which network domains should connect other domains. If you are not sure and need to transition, proceed with no worries. The network domains can be added and modified at any time.
-
If you have plans for custom network domains, follow these instructions to create them. Then, build connection policies. If you do not intend to build custom network domains, skip this section.
-
Launch an Aviatrix Transit GW and enable HA in the Transit hub VPC. As a best practice, create a new Transit hub VPC to deploy the Aviatrix Transit GW.
-
This step has two options:
-
Option A: Connect Aviatrix Transit GW to VGW. At this point, VGW starts to advertise to the Aviatrix Transit GW. Make sure you specify a different "AS" number for the BGP session of the Aviatrix Transit GW connection to the VGW. Also note that if the Transit GW and the VGW are in the same account and same VPC, VGW must be detached from the VPC.
-
A diagram for this migration path is shown below:
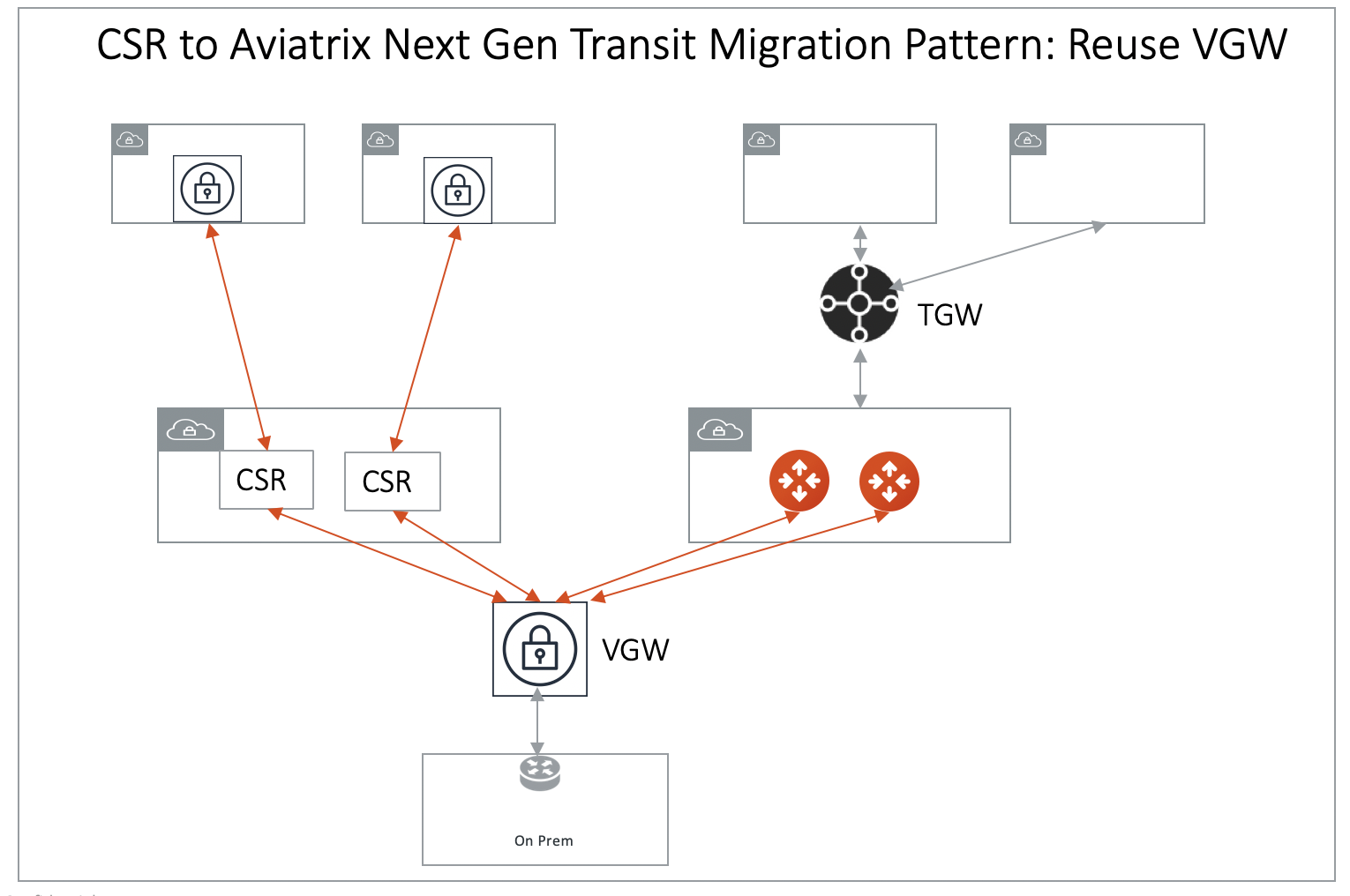
-
Option B: Connect Aviatrix Transit GW to CSR. There are certain situations where you need to keep the CSR as the connection point to on-prem (for example, you need to use CSR route summarization feature to control routes to VGW to be under 100). In such a scenario, use External Device option in Transit VPC workflow to create an IPSec and BGP connection to CSR, as shown in the diagram below. After all Spoke VPCs are migrated, delete the connection to CSR, connect the Aviatrix Transit GW to VGW.
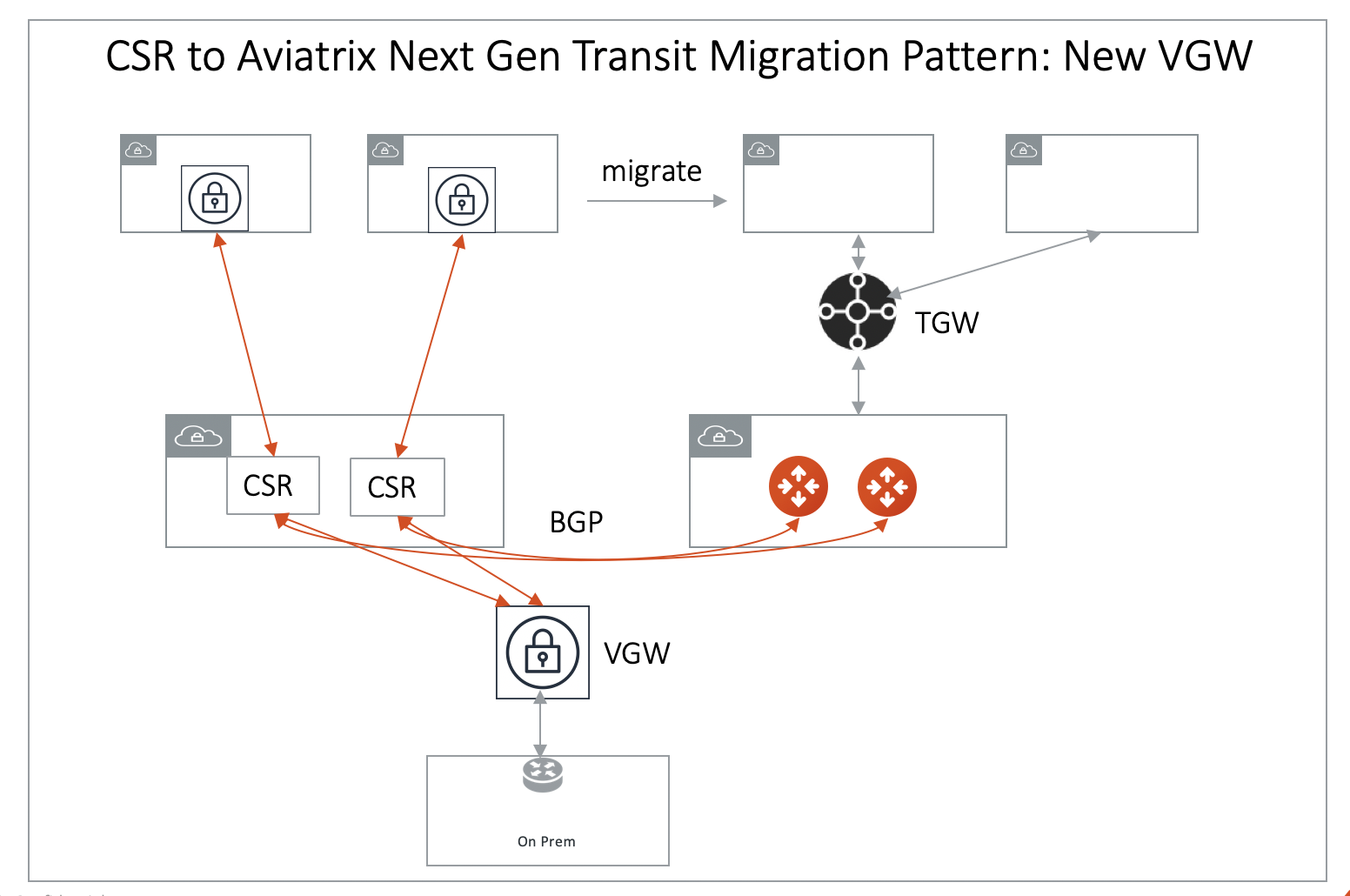
-
Remove a Spoke VPC. Select one Spoke VPC that has VGW deployed. Remove the VPC Transit Network tag. This will effectively detach the Spoke VPC from the CSR Transit Network. Make sure the above Spoke VPC CIDR route entry has been removed from the Transit Network.
-
Attach a Spoke VPC to the corresponding network domain.
-
Repeat steps 5 and step 6 for the remaining Spoke VPCs.
-
Remove the Transit Hub VGW CSR tag after all Spoke VPCs have been migrated to Aviatrix Transit GW. This effectively detaches the VGW from CSR.
The effective operation downtime for each Spoke VPC is the time between the Transit Network tag being removed for the Spoke VPC and the Spoke VPC being attached to Aviatrix Transit GW. It should be a few minutes.