Aviatrix FireNet / AWS Transit Gateway Native Deployment Comparison
There are two native deployments: TGW VPN to connect to firewall or TGW VPC attachment to connect to firewall.
The three different deployment models are illustrated in the diagram below.
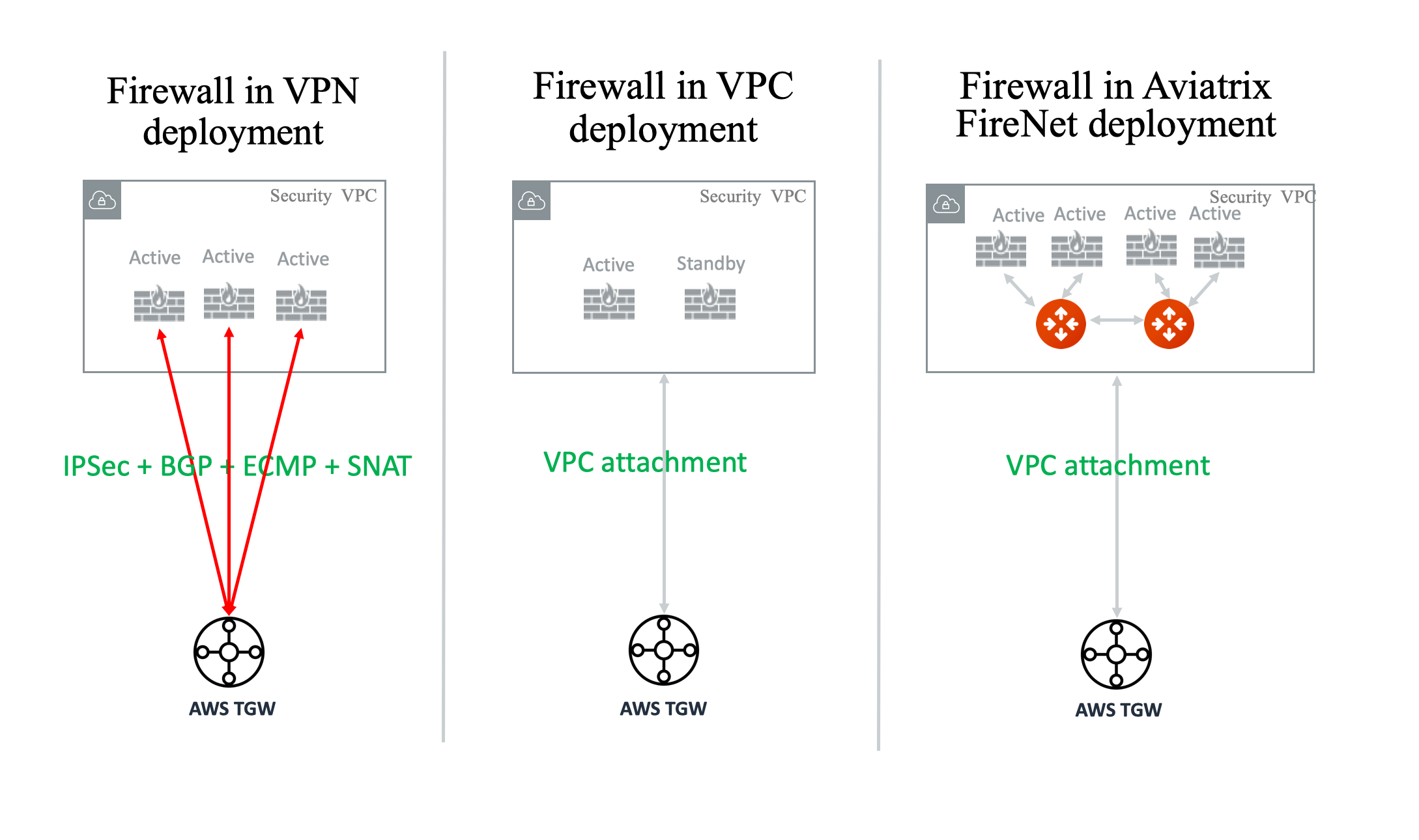
If an AWS Transit Gateway connects to a firewall by using its built in VPN function, it must run IPsec and BGP. If you run more than one firewall instance using ECMP, each firewall instance must configure SNAT function to ensure that both source and destination-initiated traffic lands on the same firewall instance. Furthermore, since native deployment requires an IPsec VPN which limits its performance to 1Gbps, in this scenario a single firewall instance can only perform at 500Mbps since the VPN function is traversed twice.
A more detailed functional comparison is described in the table below.
| Firewall Deployment Functions | Firewall in VPN deployment | *Firewall in VPC/VNet attachment | * Firewall in Aviatrix FireNet |
|---|---|---|---|
On-prem to VPC/VNet traffic inspection |
Yes |
Yes |
Yes |
VPC/VNet to VPC/VNet traffic inspection |
Yes (requires SNAT) |
Yes |
Yes |
Egress traffic inspection |
Yes |
Yes |
Yes |
Per firewall performance |
500Mbps |
Up to 6Gbps |
Up to 6Gbps |
Total FireNet performance |
> 500Mbps |
Up to 6Gbps |
up to 75Gbps |
Multiple firewalls (scale out) |
Yes |
No (Active/Standby) |
Yes |
Integrated solution |
Yes |
No (requires external script) |
Yes |
Solution complexity |
High |
Medium |
Low |
Centrally managed |
Yes |
No (requires external script) |
Yes |
Multi-vendor support |
Yes |
Yes |
Yes |