About Distributed Cloud Firewall Settings
On the Security > Distributed Cloud Firewall > Settings tab, you can configure the following:
-
Security Group Orchestration
-
Decryption CA Certificate
Security Group Orchestration
|
This feature is available with Controller 7.1.1710 or greater. If you are using Controller 7.0, you can click Manage on the Security Group Orchestration panel and enable or disable Security Group Orchestration for selected VPC/VNets. The rest of the functionality below is not available. |
When the Security Group Orchestration feature is disabled, this card shows how many VPC/VNets are available to configure.
When the Security Group Orchestration feature is enabled, you can:
-
See how many VPC/VNets have Security Group Orchestration enabled.
-
Pause the Security Group Orchestration process for VPC/VNets that have had Security Group Orchestration enabled before upgrading your Controller. After upgrading, you can resume the Security Group Orchestration process.
The states are Complete, In Progress, Completing Current Cycle, and Paused.
-
View the Security Group Orchestration configuration in the topology.
-
Click Manage to enable or disable Security Group Orchestration.
| The Aviatrix Controller will not remove original ASGs, or apply Aviatrix ASGs, on Azure ScaleSet instances. |
Decryption CA Certificate
|
This feature described below is available with Controller 7.1.1710 or greater. Aviatrix strongly recommends replacing the default Aviatrix CA certificate with your own CA certificate. If you are using Controller 7.0, you can only download the provided default Aviatrix CA certificate. The decryption CA certificate (the Aviatrix certificate, or your own) must be distributed to all of your client machines so that signature checks are successful. |
The CA certificate is used when you create a policy that has TLS enabled.
Uploading Your Own Certificate
It is best to upload your own certificate (must be in .pem format), since you likely have this certificate in use throughout your environment. You can remove the default Aviatrix CA certificate first, if desired.
-
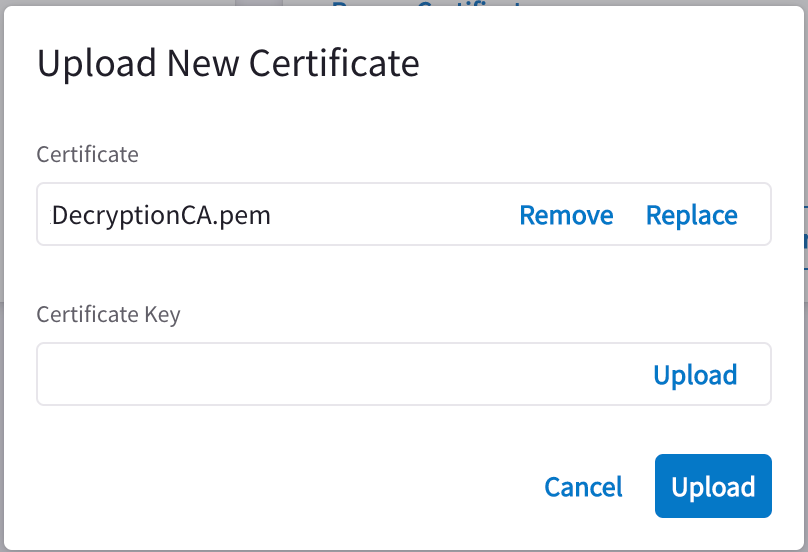
On the Settings tab, on the Decryption CA Certificate card, click the arrow next to Download Certificate and click Upload New Certificate.
-
In the Upload New Certificate dialog, you can upload, remove or replace a certificate and its corresponding certificate key.
-
Both fields must be populated. Click Upload.
You can also:
-
Download the Aviatrix CA certificate, if you want to use it
-
Download the default trust bundle (or upload your own trust bundle)
-
Determine which level of enforcement to apply to CAs that are not signed by a root certificate in the trust bundle
-
Remove a certificate and replace it with a new one
Downloading the Aviatrix Certificate
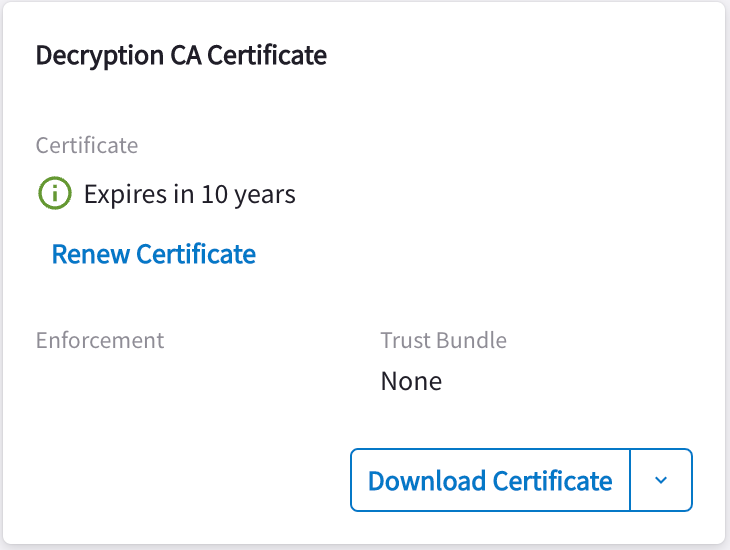
You can download the currently applied Aviatrix CA certificate and add it to your trust bundle.
To download the CA certificate provided by Aviatrix:
-
Navigate to Security > Distributed Cloud Firewall > Settings.
-
On the Decryption Trust CA Certificate card, click Download Certificate.
-
Ensure that the downloaded file is saved to the appropriate location on your computer, and any client machines involved in your Distributed Cloud Firewall configuration.
Renewing Certificate
You must renew your Aviatrix CA certificate when it is about to expire.
When you click Renew Certificate, the certificate renews automatically.
You can also upload your own CA certificate.
Trust Bundle
A trust bundle is a list of trusted CA certificates. If a gateway terminates the TLS connection and negotiates a new TLS connection to the origin certificate, then the origin certificate must be signed by one of the trusted CA certificates if running in the Strict Enforcement mode.
To upload, remove, or replace a trust bundle (must be in .pem format):
-
On the Settings tab, on the Decryption CA Certificate card, click the arrow next to Download Certificate and click Upload Trust Bundle.
-
In the Upload Trust Bundle dialog, you can remove or replace the trust bundle.
-
Click Upload.
Edit Enforcement
Use the Enforcement option to determine how Distributed Cloud Firewall handles origin certificates that are not signed by a trusted Certificate Authority.
| Aviatrix strongly recommends changing the enforcement level to Strict. |
To edit the enforcement level:
-
On the Settings tab, on the Decryption CA Certificate card, click the arrow next to Download Certificate and click Edit Enforcement.
-
In the Edit Enforcement dialog, select an Enforcement level:
-
Strict: terminate connection for incorrect signatures
-
Permissive: generate a syslog message if the certificate is not signed by a CA, but continue with the connection
-
Ignore: certificate signatures are not checked
-