Secure Networking with Distributed Cloud Firewall
Distributed Cloud Firewall uses micro-segmentation to provide granular network security policies for distributed applications in the Cloud. Distributed Cloud Firewall enables network policy enforcement between SmartGroups you define in a single cloud or across multiple clouds. In Distributed Cloud Firewall, a SmartGroup represents a logical grouping of your applications. The application(s) you include in a SmartGroup can span different cloud accounts, regions, and VPC/VNets within your Aviatrix multicloud network. You can configure policies to filter traffic between applications residing in the SmartGroups.
Distributed Cloud Firewall is supported for AWS, Azure, and GCP.
Spoke Gateway Sizing
Distributed Cloud Firewall is supported on the following gateway types:
-
Spokes attached to a Transit gateway
-
Spokes detached from a Transit gateway
Recommended Spoke gateway sizing is provided in the following table.
| Gateway Size | L4 Policy | WebGroups | IDS |
|---|---|---|---|
t3.micro or equivalent |
Yes (non-production only) |
No |
No |
t3.small or equivalent |
Yes |
Yes, in an upcoming release |
No |
t3.medium or larger |
Yes |
Yes |
Yes |
Distributed Cloud Firewall can be used to control Egress traffic by enabling Source NAT on the gateway configuration, and creating policies with WebGroups.
|
As of Controller 7.1 and CoPilot 3.11, Distributed Cloud Firewall with WebGroups is the recommended method for configuring and implementing Egress Security. This document describes Egress functionality available in the Aviatrix Controller prior to Controller 7.1/CoPilot 3.11. For information on configuring the legacy Egress FQDN solution, click here. Distributed Cloud Firewall is in Preview mode for earlier Controller versions. See Aviatrix Feature Availability by Controller Version for more information. |
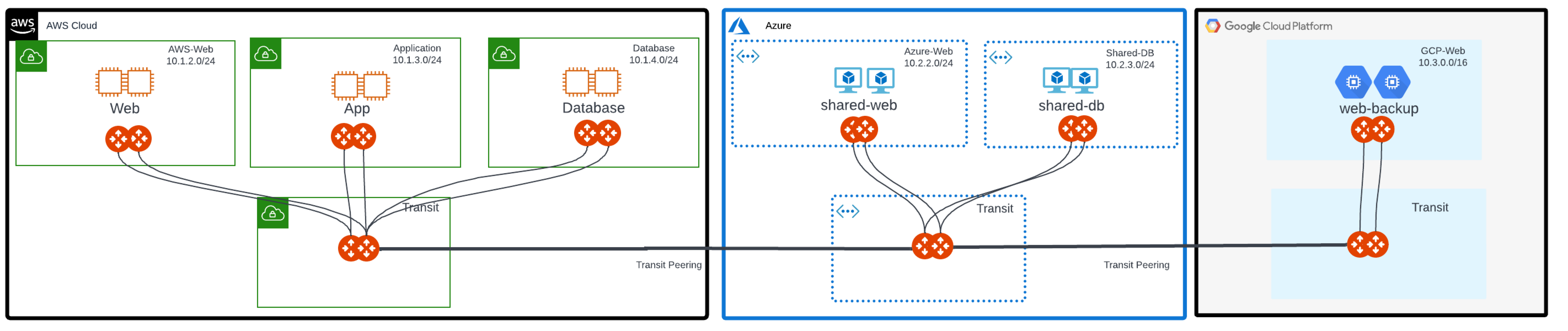
Use Cases
Use cases where you might implement Distributed Cloud Firewall are:
-
Workload isolation: in a typical tiered application, you may want to isolate tiers that do not require access to each other. For example, in a Shopping Cart application, there could be workloads for product inventory, billing, and a Product Logging app. Since the Shopping Cart application does not need to communicate with the Product Logging app, this traffic should be blocked.
-
Quarantine compromised machines: You can isolate a compromised machine by placing it in its own SmartGroup and blocking communication to that SmartGroup.
Enabling the Distributed Cloud Firewall Feature
|
If you see a message on the Distributed Cloud Firewall page (Security > Distributed Cloud Firewall) that you require the Aviatrix Universal Subscription, in the cloud marketplace you must subscribe to and accept terms for the Aviatrix Secure Networking Platform 2208-Universal 24x7 Support offer. Take note of your Customer ID for this offer. If there is no pre-existing customer ID (you are a new user), you entered this customer ID when logging on to CoPilot. You do not need to reset the Customer ID on the License tab before enabling the feature. If you have already subscribed to the Aviatrix Universal Subscription license, you do not need to subscribe again. You can just enable the feature from Configuration > Settings > License in CoPilot. |
After subscribing to the license (if you are a new user), do the following to enable the Distributed Cloud Firewall feature:
-
In CoPilot, go to Settings > Configuration > License.
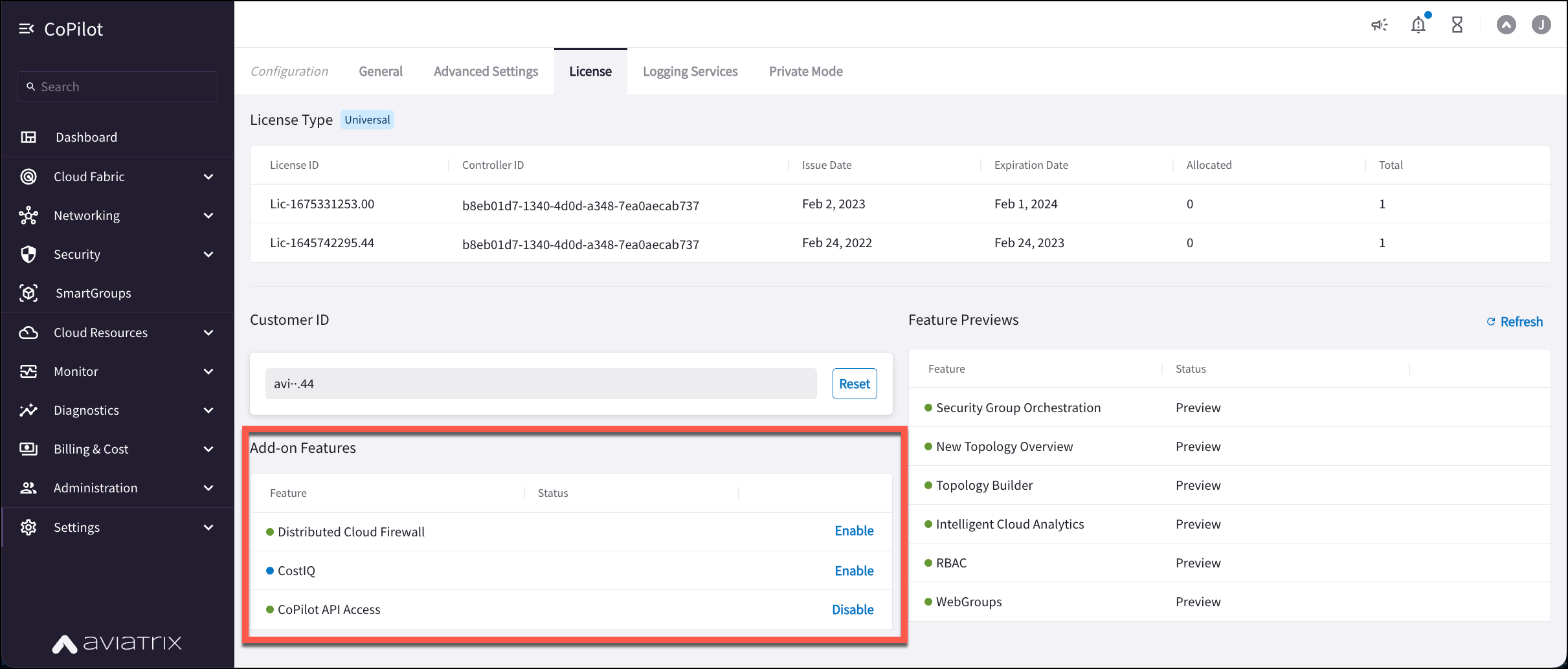
-
In the Add-on Features list, click Enable for the Distributed Cloud Firewall feature.
Enabling the Feature after Changing Licenses
If you are a current user and you change licenses, you must reset the Customer ID before enabling the feature:
-
After subscribing to the new license, log on to CoPilot and go to Settings > Configuration > License.
-
Click Reset next to Customer ID.
-
Enter the new customer ID.
-
Select the I understand the implications checkbox.
-
Click Reset.
-
Under Add-on Features, enable the feature.
Greenfield Rule
If you have not yet configured Distributed Cloud Firewall, when you first navigate to the Distributed Cloud Firewall > Rules tab you are prompted to begin using the feature.
If you have already started using Distributed Cloud Firewall, you can skip this section.
| You must first have created your WebGroups. |
-
Click Begin Using Distributed Firewall.
-
A message displays indicating that a Greenfield Rule will be created to allow traffic that maintains the current state, which facilitates the creation of custom rules for specific security needs.
-
Click Begin. The Greenfield Rule is added to the Rules list. This rule prevents traffic from being dropped before you start configuring the rest of your rules. By default (if you selected the recommended Permit All Traffic option), the rule has the following attributes:
-
Source/Destination SmartGroups: Anywhere (0.0.0.0/0)
-
Protocol: Any
-
Action: Permit
-
Logging: On
-
After you create additional rules you can move the Greenfield Rule where needed in your rule priority list.
You can delete the rule later if desired.
| The Greenfield Rule is only enforced on gateways, and not on Security Groups in the cloud. |
Editing the Greenfield Rule
To edit the Greenfield Rule, click the pencil icon next to the rule. You can edit the following fields and click Save in Drafts.
-
Source and Destination SmartGroups
-
Protocol
-
Action: Deny or Accept
-
TLS Encryption: On/Off
-
Enforce: On/Off
-
Logging: On/Off
-
Rule Priority
When you are ready to commit the rule, click Commit.
Prerequisites
Before applying Distributed Cloud Firewall:
-
Your version of CoPilot must be 2.0 or greater.
-
Your version of Aviatrix Controller must be 6.7 or greater.
-
Gateways must have their image updated to version 6.7 or greater.
-
Network reachability should be configured between the VPCs that contain applications that require connectivity. You configure network reachability using Connected Transit/MCNS.
-
Enable Egress on the Spoke Gateways used in
-
If you plan to use cloud tags in your SmartGroups, Cloud resources must be tagged appropriately.
-
You must have already created WebGroups, if you want to use them in your Distributed Cloud Firewall configuration.
Distributed Cloud Firewall Components
Distributed Cloud Firewall introduces two important configuration components—SmartGroups and policies.
Configuring Distributed Cloud Firewall
To configure Distributed Cloud Firewall, click here.